Microsoft released an out-of-band emergency security update for Internet Explorer on September 23, 2019 for all supported versions of Windows.
The emergency update is only available on the Microsoft Update Catalog website at the time of writing and not through Windows Update or WSUS.
Some support articles provide little information. The Windows 10 update description simply states "
Updates to improve security when using Internet Explorer" without going into further detail. The page links to the Security Update Guide which, after some digging, leads to the CVE of the vulnerability.
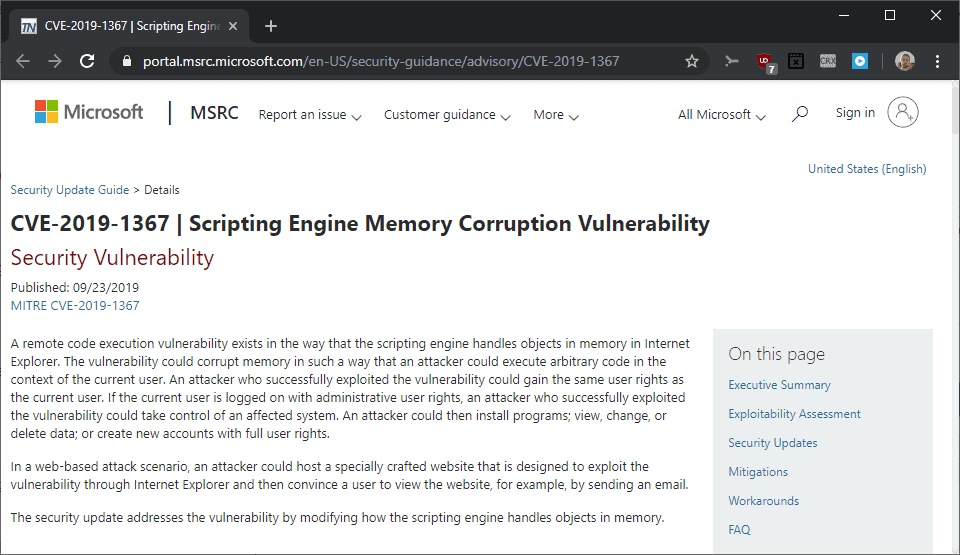
The support page for the cumulative update for Internet Explorer offers more information and a direct link to the CVE.
It states:
This security update resolves a vulnerability in Internet Explorer. A remote code execution vulnerability exists in the way that the scripting engine handles objects in memory in Internet Explorer. The vulnerability could corrupt memory in such a way that an attacker could run arbitrary code in the context of the current user. The security update addresses the vulnerability by changing how the scripting engine handles objects in memory.
The same information is provided on the CVE page as well. Microsoft notes that an attacker could take control of the attacked system if the attack succeeds which would allow the attacker to install or remove programs, view, change or delete files, or create new user accounts.
The security issue is exploited actively according to Microsoft; an attacker could create a specifically prepared website to exploit the issue in Internet Explorer.
Microsoft published a workaround to protect systems if the released updates cannot be installed at this point. The workaround may reduce functionality "for components or features that rely on jscript.dll".
The commands need to be run from an elevated command prompt.
Workaround for 32-bit systems:
- takeown /f %windir%\system32\jscript.dll
- cacls %windir%\system32\jscript.dll /E /P everyone:N
Workaround for 64-bit systems:
- takeown /f %windir%\syswow64\jscript.dll
- cacls %windir%\syswow64\jscript.dll /E /P everyone:N
- takeown /f %windir%\system32\jscript.dll
- cacls %windir%\system32\jscript.dll /E /P everyone:N
The workaround can be undone by running the following commands from an elevated command prompt:
Undo 32-bit:
- cacls %windir%\system32\jscript.dll /E /R everyone
Undo 64-bit
- cacls %windir%\system32\jscript.dll /E /R everyone
- cacls %windir%\syswow64\jscript.dll /E /R everyone
List of updates that fix the vulnerability:
What about Windows Updates?
Microsoft has not released the update via Windows Update or WSUS. Susan Bradley notes that the company could release the update on September 24, 2019 via Windows Update and WSUS but that has not been confirmed by Microsoft.
It is a bit puzzling that Microsoft releases an out-of-band security update that addresses an issue that is exploited in the wild but chooses to release it as an update that needs to be downloaded and installed manually only.
Closing Words
Should or should not you install the update right away? It is a security update but it is only available via the Microsoft Update Catalog website at the time of writing.
I still would recommend installing it but you should create a system backup, e.g. using Macrium Reflect or Paragon Backup & Recover Free, before you do so as one never knows these days updates introduce unwanted side effects or issues of their own.
Now You: install or wait, what is your position?
Summary

Article Name
Microsoft releases emergency Internet Explorer security update
Description
Microsoft released an out-of-band emergency security update for Internet Explorer on September 23, 2019 for all supported versions of Windows.
Author
Martin Brinkmann
Publisher
Ghacks Technology News
Logo

https://www.ghacks.net/2019/09/24/microsoft-releases-emergency-internet-explorer-security-update/
2019-09-24 05:04:19Z
52780389996119
Tidak ada komentar:
Posting Komentar